There is really no shortcut for testing your network against a ransomware attack. The only way to know how protected you are, is to test your defenses against real ransomware. We developed a ransomware simulator that will encrypt data on the network, but in a way that’s under your control, has an off switch, and allows you to decrypt the data as well.
PowerShell Encrypter/Decrypter
This PowerShell script will do exactly what ransomware does, encrypt files. This is the only way to truly know if you are protected.
WARNING: This tool encrypts files. Please use responsibly. If you are unfamiliar with PowerShell DO NOT use this tool.
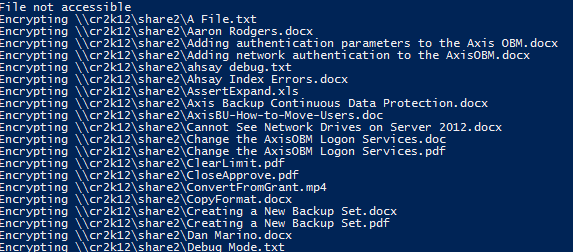
We have written two PowerShell scripts which act as the ransomware simulator. One script encrypts the data, and the other script decrypts the data using a public/private key pair. We created these as a tool, so that you can test your defenses against actual ransomware. The purpose of the decrypter is to ensure that your files aren’t permanently destroyed.
- The network drives are enumerated and sorted in descending order.
- The lowest drive letter will be attacked. This gives you the ability to control what shares are affected. In our testing environments, we use the drive letter Z as our ‘attack’ drive.
- All files are discovered. Only files are discovered, folders are excluded.
- Each file is encrypted with the Public key of our certificate. You will need a certificate for this to work and we’ve included all of the necessary steps below.
- After all the files have been encrypted, the script exits.
Are you protected?
Protect your network from the inside-out. Prevent your valuable data from becoming completely exposed to cyber criminals.
