Deception Technology has come a long way since the first honeynets of the late 90’s; however, one product that hasn’t gotten better, even though it has had a 10 year head start, is antivirus. Expert reviews of even the best antivirus products continue to be lackluster with no real winners in sight. Let’s take a look at why Deception Technology used by Canauri™ does a much better job at detecting and stopping a ransomware attack when compared to the best antivirus products on the market.
Where Antivirus Falls Short
Antivirus is a signature-based solution that cannot protect against zero-day threats. A signature is created by running an algorithm against a known virus file and then generating a hash that represents that virus’s signature. Once a signature has been created, that signature can be distributed to antivirus software through an update, and it will then protect against the threat. However, antivirus software will not protect against a zero-day threat. A zero-day threat is an attack against an unknown security vulnerability that software developers are not yet aware of. Since the developers are oblivious to the vulnerability, there would be no known security fix and subsequently no AV signature to detect it.
Bait Files Detect What Antivirus Cannot
Canauri doesn’t rely on signatures; rather, it uses Deception Technology in the form of bait files to detect a ransomware attack. Waiting for signature updates to be protected from the latest threats isn’t necessary. Cryptostopper monitors your network file shares by placing hidden bait files in your shares. It then monitors these bait files and uses a proprietary algorithm to determine if a ransomware attack has commenced. If ransomware does strike, Canauri stops the infection by isolating the infected workstation from the network and shares, sending a command to shut down the workstation, while also notifying the administrator that an attack has occurred. That notification includes vital information such as the IP address of the workstation where the ransomware attack was launched and the user logged in at the time.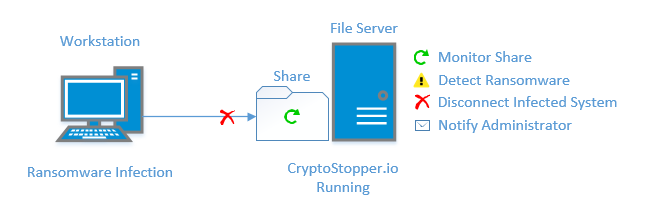
Deception Technology, the Clear Winner
It’s easy to see why antivirus that relies on signatures is the old way of detecting threats. Developed when malware was clearly not as malicious as it is today, antivirus cannot compete with the current environment that has new malware being developed every minute. Deception Technology, using bait files to deceive ransomware into revealing itself, is the simplest and best line of defense.
Further Reading:
